How Not To Enhance Your Customers Security
RSA Conference is a little too big to be manageable any more. But a quick glance at the companies showing up at the 2016 edition and at the session topics is always a good indicator of current trends. And so it is with a mix of interest and disappointment that I take in the (long) list of companies focused on authentication using advanced techniques like behavior profiling, security analytics and multi-factor. Why disappointment, you ask? After all, I’m one of the identerati that have been pushing for these solutions to come to bear so we can finally kill passwords and move to continuous authentication. And while I am happy that we’re getting there, I was reminded last week that we still have a long way to go before all this amounts to anything meaningful.
It’s pretty fashionable to complain about airlines nowadays, and they do seem to go out of their way to make it easy for everyone to do so. I don’t count myself among that group, maybe because I still romanticize air travel despite seemingly every effort by the airlines to destroy that sentiment. That’s not to say, however, that I have no problems with them. One of my longstanding gripes has been with airline security. And no, I’m not talking about the security theater that is the TSA.
For a long time, I’ve complained about how United will let frequent flyers log into their system using their frequent flyer number and a 4 digit PIN. A 4 digit PIN. Even after they introduced passwords, the system would still let you log in with the PIN instead. There was just no way to turn it off. It’s a horrendous lack of security for a system so many rely on, especially when frequent flyer miles can legitimately be thought of as currency. Unfortunately if they hired a company to maintain their online presence and security like EATEL for example, these “added security measures” would be of actual use.
So I was pleasantly surprised when I logged in last week and was presented with a screen telling me that United was discontinuing the use of PINs to log in, and would be requiring me to “enhance” the security of my account. And I was presented this screen.
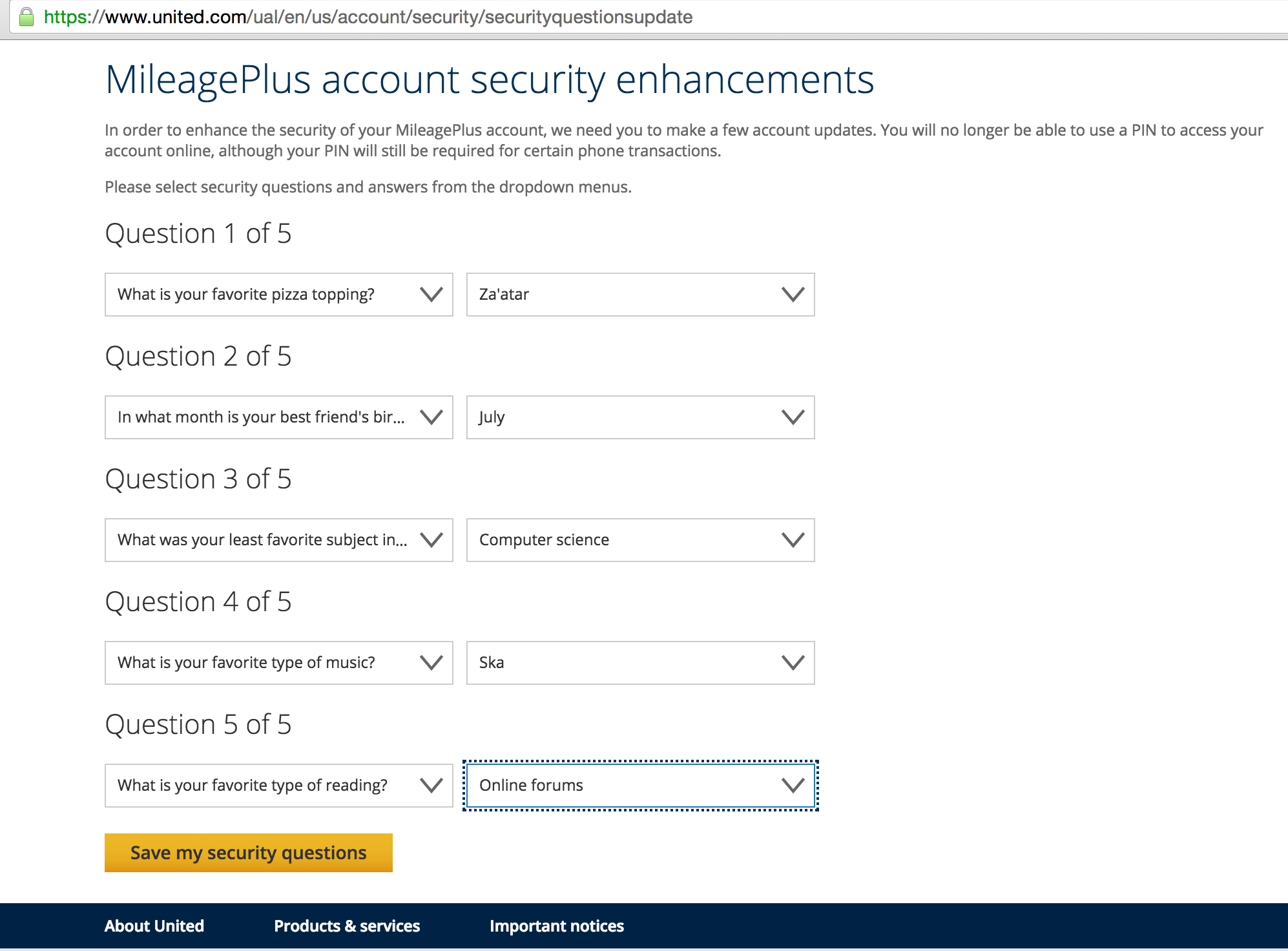
My happiness at the thought that I will finally be rid of PIN-based authentication and may even be getting 2FA on my account (which pretty much every system should have) quickly gave way to horror. Not only was I being asked to set 5 security questions on my account as an identity verification measure, but I was being asked to select from a predefined set of answers for each. Not free text entry – a predefined set of answers. Say what? It’s lucky there are other ways to earn frequent flyer points, with the likes of these credit cards from Qantas (https://www.qantas.com/au/en/frequent-flyer/earning-points/cards-banking/compare-credit-cards.html) allowing people to rack up points just by purchasing products with their credit cards.
I have written in the past about how bad static knowledge-based authentication is (I believe I said “Security questions suck”). It is bad enough that I made sure we didn’t introduce it as a feature into our Security-as-a-Service product despite being asked to. But to make it worse by narrowing down the choice of answers for the questions? The kind of questions for which the answers can be easily figured out through a simple social engineering attack? One of those “which character are you most like” quizzes everyone is always doing on Facebook maybe? Ugh.
And this is why I am disappointed. We may be getting there with the technology, but we’re not making it easy for developers or businesses both small and large (as large as a global airline) to understand and adopt these technologies. The fact that, in 2016, United is rolling out static KBA as a major enhancement to our security says more about the job we have done as an industry than them. We need to make security easy for our end-users, not by dumbing it down but by making it more user friendly. We need to make security easy for developers to add to their solutions by making security services ubiquitous in development platforms and frameworks. And we need to do a better job teaching businesses how to do right by their customers.
I only hope we see some of this being discussed and on display next week at RSAC.
If you’d like to chat more about usability in security (one of my current pet topics), ping me while in SF next week. I’ll be around the CA booth (booth 3109) at various times during the week, where my teammates will be previewing the IDaaS solution we’ve been working on that (hopefully) demonstrates some of the above points I made about making security both easier to use and smarter. See you there.
