Epic Hacking Redux: The Hacking of DeRay and Our (Continued) Identity Challenge
Almost 4 years ago I wrote a post titled ‘The Epic Hacking of Mat Honan and Our Identity Challenge‘. In it I examined how hackers exploited the ways in which our online accounts are daisy chained together through poor password recovery and KBA based systems to systematically take over Mat Honan’s digital life.
4 years later, much has changed and yet much remains the same. The hacking today of racial justice activist DeRay Mckesson is a clear example of that. Much like in the Mat Honan case, the hackers had a clear objective – getting control of his Twitter account. To do so they followed the same process of working backwards to the root in the daisy chain of account recovery systems to take it over. But the differences illustrate very clearly one of the main issues we continue to have – our authentication systems are still woefully inadequate when faced with even a slightly motivated hacker.
![[Image of DeRay from NY Times]](https://blog.talkingidentity.com/wp-content/uploads/2016/06/DeRayOnTwitter.jpg)
Anatomy of the Hack
[The following is based on what I know so far, and details may emerge/change.]
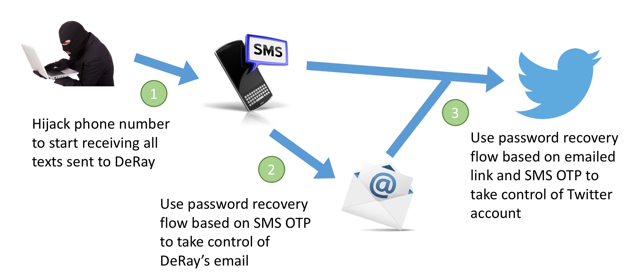
The hackers basically wanted to make sure that any text messages sent to DeRay’s phone number would get sent to a device they had instead of the phone DeRay has. To do this they called up customer service at Verizon, DeRay’s mobile provider, passed the KBA-based identity verification process, and then got customer service to reset the registered SIM information on DeRay’s mobile account to the one in the device they had. How did they pass identity verification? They knew the last 4 digits of DeRay’s social security number, something that has become incredibly easy to figure out thanks to the many breaches like the Anthem breach, or you could just calculate it.
Once they had their own device receiving texts, they essentially had control of DeRay’s second factor. Which still leaves the first factor – the password. Once again, password recovery processes to the rescue. Or in this case, the opposite of rescue.
The password recovery process for Twitter, when provided with the Twitter handle and the phone number, will show something like “Email a link to fi*******@domain.com”. So the hackers would still need to have access to DeRay’s email. The following tweet from DeRay indicates that his email was hacked too.
So one could deduce that the hackers first took over his email accounts so they could receive the password reset link that Twitter sent out. But how did they get into his email accounts? While this information hasn’t been released yet, I would guess using the hijacked phone number. In other words, they probably initiated a password recovery flow on the email account, and all they needed to reset the password was the OTP sent by text message to the phone number associated with the email address, which they now controlled.
Having control of the email account, they were now able to initiate the password recovery flow on Twitter, which sent a password reset link to the email account, which they were able to use to change the password and verify the changed password using the OTP they received by text message. And there you have it – one pwned high profile Twitter account.
What Does This Attack Reveal?
The factors we rely on to verify identity are (still) useless
It may be a better security question than “What is your aunt’s maiden name?”, but last 4 digits of social security number is definitely not enough to verify someone’s identity over the phone. It’s far too easy to search for, buy on the dark web, or socially engineer and phish someone’s personal information now. And SSN can just be calculated. KBA is deader than a Norwegian Blue. This is why it’s still so important that we know where our nearest Social Security office is, such as the North Dakota Social Security office, should we ever be in a situation where our SSN has been stolen and we need to report it.
Bad processes are still a huge attack vector
Who would have thought that something as significant as resetting the SIM information on a mobile account would be as easy as paying the bill, with security being sacrificed to enable better customer service?
‘Forgot Password’ is still the weakest link
As long as passwords are the first and main factor in authentication, the password recovery process is going to continue to be the weakest link in the entire connected web of our digital lives.
2FA that relies on SMS-based OTP is already defunct
Google knows this, and have published a paper with their research findings on this. Banks already don’t consider SMS-based OTP good enough. Maybe it’s time for everyone else to move on too.
CTA: Make Invisible Identity Happen
This is such a clear example of why we need to built the Invisible Identity platform I presented at the Cloud Identity Summit. At its center, Invisible Identity relies on Continuous Authentication. Would this attack have worked if the Verizon identity verification flow for something as significant as resetting the SIM included an email verification link or, better yet, a voice biometric? What if Twitter relied on a combination of soft tokens and passive factors like geolocation and device fingerprinting? This hack wasn’t a simple phishing hack. It required effort from the hackers – to get the SSN info and to hijack the mobile number. But would adding continuous authentication into the mix have made the barrier too high for their tastes?
4 years ago, the hack of Mat Honan wasn’t a drive-by. It wasn’t a password discovered in the massive password dumps that was used by a script going around trying to lock accounts up for a small ransom. Mat was targeted, and in the aftermath of the attack, he put in place additional protections on his accounts – the kind DeRay had on his. DeRay was a responsible and smart account owner that did all the right things – including setting up 2FA in the systems. And yet it didn’t help. 4 years on, things should be a lot better.