Multi-Factor Authentication going Mainstream
Some recent moves by major players could have a significant impact on the perception of multi-factor authentication technologies.
- Google recently introduced two-factor authentication for Google Apps. The mechanism they chose to employ relies on a one-time password token delivered to a cell phone either by an SMS text message or a call to the phone (anyone that has signed up for Google Voice and tried to add a phone number will be familiar with the call-based mechanism). Google combines the OTP mechanism with device authentication (“trusted” devices like a desktop computer won’t require the second factor, while a work laptop that can get stolen, and therefore misused, will). So enterprise use of Google Apps just got a lot more secure.
- Meanwhile, Windows Live has introduced essentially the same mechanisms in their account recovery process for Hotmail accounts.
These recent developments provide very good proof-points for how multi-factor authentication can easily be incorporated into IdM programs in a user-friendly manner. As part of the Oracle Identity Management suite, Oracle Adaptive Access Manager provides enterprises the capability to roll out the same features (among many others) as part of their access management program, giving them the ability to leverage two-factor authentication in a simple form factor.
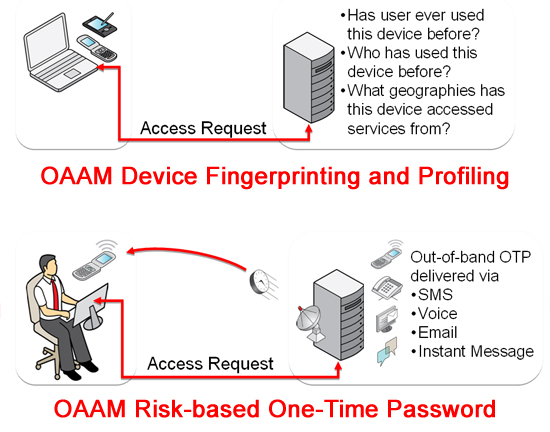
In fact, the ability to step up authentication using different channels as part of a risk-based identity management program that takes device identities into account was a major component of a demo we did last week at OpenWorld. The demo, in IdM VP Amit Jasuja’s session on “Oracle IdM 11g Review & Future Directions”, highlighted the potential for identity to power the next-generation mobile workplace. The basic idea was that any time a transaction is identified as being high risk (a user modifying core privileges of a role, doing an in-application privilege elevation request, or accessing the application from a previously unused computer), the access management system can force the user to re-authenticate to the system using a mechanism that is distinct from what they used initially (like logging in using SSO).
The key differentiator here is “risk-based“. While OAAM can provide enterprises a cost-effective alternative to hardware token based MFA, it doesn’t stop there. It also allows enterprises to bring in advanced real-time risk analytics, proactive actions, investigation tools and robust customizable reporting. The result is a comprehensive tool for managing security and risk as part of your enterprise’s overall identity management and governance programs.